Usb dongle crack - How to install HASP MultiKey USB Dongle Emulator on Windows.


Wibu

On the other hand, some of the links contain the malicious virus which is very harmful to your device. You can also use our to send us dump file directly and securely. Electronic signatures are kept on such dongles. I searched on Internet and read many web pages regarding dongle emulator. After Windows is booted it will install the unsigned driver automatically. Dongle Tools Before you download these tools, please note that I am not the author of any of them. Besides, the olde-qate will be better for preventing any kind of problem.
Safenet Sentinel Usb Dongle Crack
-508x696.jpg)
The test version the old one but it comes with many useful features. Please do not ask me for 'cracks' for any dongle protected programs, whether featured here or not, I won't help you. I work and use bluetooth for calls coming in at home. It is for that, using this type of multi-tool the data of your device can be deleted. There can be up to 10 different passwords but it doesn't mean that all dongles are connected to computer.
Wibu

A dongle is a piece of hardware that attaches to a computer and allows a piece of secured software to run. Programs that use dongles include computer-aided design , image rendering, and audio mixing software. This is exceptionally valuable apparatus for windows it helps a great deal in the opening Mobile. The idea of the system is that the software will only operate when a specific, unique device is inserted into the computer. The idea is that it is much harder to reproduce a physical item such as a dongle rather than the software itself. If you have any problem, please drop a comment. Now, I want to write some steps here: Note: I cloned successfully all types of dongles with MultiKey Emulator.
Safenet Sentinel Usb Dongle Crack
Then only pay for dongles as you need them. Your phone is ready to use. Running your software To find your key it is necessary to start protected software. We do have digitally signed emulator that doesn't require Test mode on your computer. Usually it doesn't take more than 24 hours. Well if you are an experienced motor bike driver also you might slip on these. Im doing all kind of programms and databases, Networking, Web development, also project management softaware.
How to Crack Dongle, Hardware lock USB or Emulate
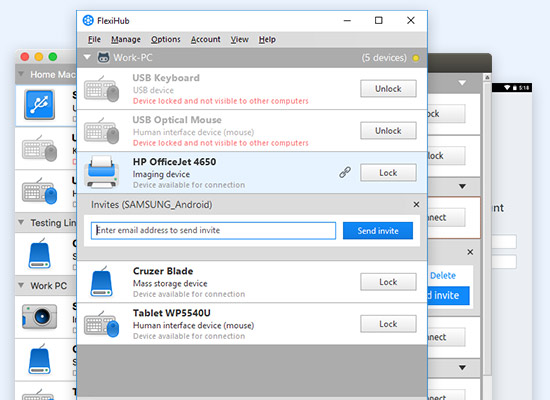
Feel free to share and comment. Encryption works with WibuKey set of rules 3 or 5 relying at the nonvolatile saved Standard Entry. I tried this on Windows 32 machine for sentinel hl max. Of course some of the developers are kind enough to supply wonderful little utilities such as the example above from Cimagrafi. I won't do it, and I'll probably lecture you. This software is available on various websites.
Dongle Emulator, Clone and Crack Service
If rain falls or the waves comes in, the roads become really slippery, so does the bumpers. Sending dumps and getting trial version Please send created dump files to We'll send trial version of as soon as get your mail. Very few programs designed for the general public use this security method. This will boot your device in the download page. So, you need not tense about it. While loading, the software would check for the presence of this hardware device and, if it did't find it, it wouldn't load.
Share USB dongle over Network

This is almost certainly where the future of the market lies, well implemented smart card technology is likely to be far more immune from both software and hardware reverse engineering, however the reversing of such devices will still be within the budget of most corporations. The program no longer opens without the dongle and now all of my drive test files cannot be read. It should show Now you can start your protected software and enjoy it. In some cases, the computer running the software must have an Internet connection so that it can regularly connect to the manufacturer's servers to confirm who is using the program. Then extract the file to the C folder of your computer.
reverse engineering
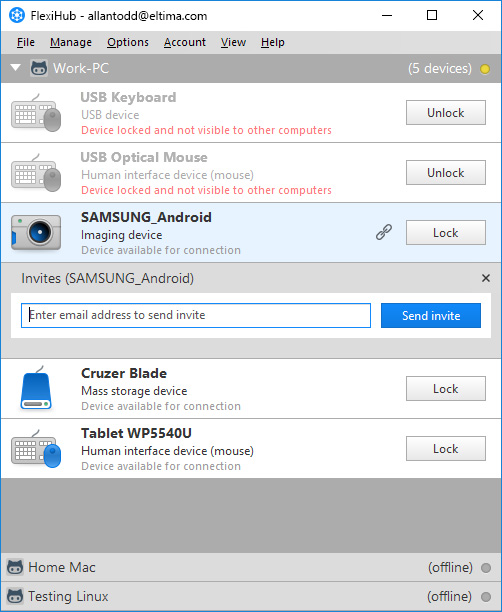
Users want just the opposite — to make using software as simple and convenient as possible, no extra security layers or tricks, please. The original meaning of dongle was a device used as a security system. Software solutions that claim to backup dongles are actually emulators, crackers. Bluetooth Dongles pass information between two computers and more, homepage smartphones, and other devices — no extra cables or cords are required. I should point out that removing dongles from software is legally a slightly different area to debugging standalone applications even if you have purchased a legitimate dongle , read either or homepage the legal directives regarding hardware locks the second link there is a little German biased , note that if your dongle is stolen you are left up the creek basically, pay for a new one or else. The interface of this tool is simple and you can flash or repair your device with this tool without any difficulties. By attaching it to a computer or another electronic appliance a user can unlock software functionality or decode content or access a hardware device.
USB
This keeps us away from going to the market to repair our Android device and spend money. All Sentinel shells are vulnerable to either a known plaintext attack or brute force. The system means that the software is set up to only run after confirming that the dongle is inserted in the machine. Nothing black-market here no any file, crack, patch, codes, keys, generators, electronic device emulators links here , this can be solely web site links resource as thousands different websites. Just drop us e-mail to to receive payment details. A mobile dongle, for example, includes a that allows a computer to connect to the Internet. A software protection dongle is a device that allows you to protect content from accessing and copying.
UNDER MAINTENANCE